The appearance of the software program revolution has introduced unprecedented productiveness and comfort. Nonetheless, it has additionally led to an elevated menace within the type of hacking and knowledge breaches.
Forging a signature is without doubt one of the oldest types of fraud within the guide and might be the quickest approach for a legal to persuade a authorized or enterprise establishment that they’re somebody they’re not. Due to digital signature safety, we lastly have a method to confirm on-line actions.
What’s a digital signature?
A digital signature is a cryptographic method used to confirm the authenticity of digital paperwork, messages, and transactions. It solves the issue of tampering, alteration, and impersonation. Digital signature safety is maintained by way of uneven cryptography.
On the floor, the transfer from the normal written signature to digital signature software program for conducting enterprise appears to have made this malicious imitation simpler than ever. In any case, the bodily artistry of crafting a signature was changed with easy stylus strokes and pictures.
Fortunately, this challenge has been on the forefront of IT consultants’ and e-signature software program corporations’ consciousness. Safety of identification and knowledge is by far one of the vital necessary elements of their enterprise fashions.
Regardless of this, not all software program options are created equal, so it can serve you properly to develop an understanding of what safety measures are essential to defend your corporation and shoppers.
How digital signature works
On the core of all these types of knowledge safety is the digital signature. A digital signature is separate from the conventional e-signature in that it’s not a illustration of a ‘formal’ bodily signature and isn’t used for notarizing enterprise and authorized agreements.
As an alternative, a digital signature is a safety software consisting of a fancy mathematical algorithm used to confirm the authenticity and validity of a message despatched over the web.
E-signature software program makes use of digital signatures to be able to present elevated safety to its customers. The essential operate of this course of is to offer two units of digital “keys” for a doc utilizing what is named the general public key infrastructure system (PKI).
The primary key’s a public key that the sender of the doc holds, whereas the second is a personal key that’s generated by the act of signing the doc itself.
When the notarized doc is returned to the unique entity, the embedded cryptographic algorithm will evaluate the 2 keys. If the personal key despatched by the signee doesn’t match the general public key held by the recipient, the doc will stay locked.
This straightforward encryption course of is nonetheless an especially efficient approach to make sure that an digital signature stays safe and that the data of offers and agreements made are correct and reflective of the particular state of affairs for both a enterprise or one other authorized entity.
Varieties of digital signatures
Whereas the usual PKI system is usually greater than sufficient for many companies, some organizations work with extraordinarily delicate knowledge and wish additional layers of safety for the agreements they deal with.
Licensed signatures
Licensed signatures are like typical digital signatures in that they’re used to notarize authorized and enterprise paperwork. Nonetheless, in addition they embody an extra degree of safety and assurance within the type of a digital certificates.
These certificates are issued by a 3rd occasion generally known as a Certificates Authority (CA) and assist the recipient confirm the origin and authenticity of the doc in query.
Approval signatures
Approval signatures operate just a little in a different way than different types of digital signatures.
In actual fact, they aren’t issues that the ultimate recipient supposed to signal in any respect. Quite, they operate to suggest {that a} specific doc has been permitted by a specific individual or entity in order to forestall pointless correspondence and optimize workflows and bureaucratic processes.
Invisible signatures
This type of digital signature permits a sender to switch a sort of doc the place the visible illustration of a signature won’t be applicable whereas nonetheless verifying that it has been permitted by the correct individual (within the case of an approval signature) and/or had its authenticity licensed.
The selection between offering a visual or invisible digital signature is usually determined by particular firm insurance policies and the way a lot info you need to present to a signee.
Courses of digital signatures
Along with the varied forms of digital signatures, there are additionally particular tiers of digital safety, ranked from least to most safe. The presence of particular safety features could affect the rating of a specific answer and are tied to the general strategy of signature certification mentioned above.
Class I
The primary tier of digital signatures, class I signature certificates, present a fundamental degree of safety and are usually solely validated based mostly on an e-mail ID and username. Due to this, the signatures tied to this should not legitimate for authorized paperwork or most enterprise agreements.
Class II
The second class of digital signatures is usually used for securing taxes and different monetary paperwork and data the place the danger and basic safety considerations are low or reasonable.
Class II signatures operate by evaluating a signee’s identification in opposition to a safe database to be able to assist management who has entry to what particular info.
Class III
The third and closing tier of digital signature safety comes within the type of on-line “checkpoints” that require a company or individual to current a selected type of identification, similar to a driver’s license, earlier than they can signal the settlement or doc in query.
One of these signature safety is used for issues similar to courtroom filings, e-ticketing, and different areas the place a excessive degree of safety is required.
Digital signature safety features
Whereas these basic ideas will definitely pay themselves again many occasions over the course of your profession, typically you simply want to guage a specific piece of e-signature software program based mostly on the nitty-gritty of the specs.
Under is a listing of various options associated to doc and signature safety meant to assist information your search as you discover methods to make sure the integrity of your knowledge.
PINs, passwords, and codes
This primary characteristic is by far probably the most fundamental and easy; nonetheless, its close to ubiquitousness is a testomony to simply how efficient it’s as a base degree of safety and is itself deceptively complicated.
Through the use of a doc that’s protected by a password despatched out by the doc proprietor, you’ll be able to assist the signee know what they’re signing is real whereas stopping undesirable doc tampering on the identical time.
Cloud safety
With a lot, if not all, of digital signature software program being delivered underneath the Software program as a Service (SaaS) mannequin, it’s essential to ensure you know what to search for with regards to the safety protocols that can be remotely deployed to be able to defend your authorized and enterprise agreements by the seller itself.
Understanding previous safety breaches, knowledge loss, and different dangers is essential if you wish to make your best option doable to your group. This may be completed in a couple of methods.
First, you need to be sure that the seller in query is utilizing a robust cloud infrastructure, normally by way of a partnership with service suppliers similar to Microsoft Azure or IBM SoftLayer. The good thing about that is that it ensures the baseline safety infrastructure of a vendor meets the varied regulatory necessities for top-of-the-line digital safety.
The subsequent piece of the puzzle comes within the type of understanding the best way wherein the software program vendor approaches knowledge encryption. For this, there are two key phrases it is advisable to perceive:
- Resting Information: Information that’s stored in a cloud server or on a tough drive that is not at the moment being accessed by a program.
- Transit Information: Information in transit refers back to the motion of information between servers and purposes.
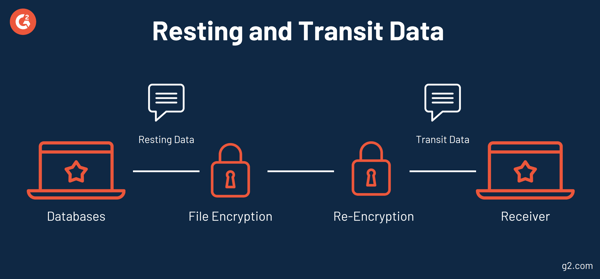
So as to have really complete cloud safety, it is advisable to be sure that the seller you are contemplating has robust knowledge encryption each throughout the remainder and transit section of the information lifecycle. It will assist defend present offers and agreements in addition to make sure the safety of data and documentation.
Consumer authentication
One other method to rapidly and successfully guarantee an extra layer of safety to your paperwork and agreements is to implement options to assist confirm the identification of the supposed signee.
These options embody instruments to authenticate a signee earlier than they execute their digital signature, in addition to a way to tie that authentication to the general e-signature document.
Ideally, an answer using an excellent set of person authentication protocols will permit for a number of authentication strategies similar to distant ID and password authorization, e-mail handle verification, or doc uploads similar to a driver’s license or different official authorities documentation.
Timestamping
Timestamps are normally related to licensed signatures as a method to visually show the verification of a specific doc or settlement.
The presence of a digitally approved timestamp signifies that the contents of a file have been verified at a given time by a specific individual or entity and haven’t modified since. These stamps are fetched and utilized by way of an automatic service that’s related to the digital signature certification course of.
Embedded audit trial
The flexibility to independently confirm and archive an digital signature can present a vital layer of safety for your corporation.
This course of is achieved when a chunk of e-signature software program embeds the signature immediately into the doc itself, making a self-controllable, transportable document free from the affect of the unique software program vendor.
The general impact of that is to make sure full management over your data and paperwork so {that a} change in account with the seller won’t have an effect on your skill to entry data.
E-Signal compliance guidelines
Now that you just’ve developed an understanding of the safety features you want to be able to defend your knowledge, the following step is to make sure your digital signatures stay compliant with the varied regulatory oversights of your group or trade.
Sure authorized necessities have to be met to your digital signature to operate as a legitimate enterprise course of.
These are included in the USA E-Signal Act, which gives digital signatures with their authorized standing.
- Intent to signal: Like with a standard signature, this refers to the usual authorized situation the place a signature is barely legitimate if all events intend to signal.
- Consent to do enterprise electronically: For an digital signature to be thought-about legally binding, all events should conform to register a digital format.
- Affiliation of signature with the document: The subsequent a part of making certain E-Signal compliance is to be sure that the software program answer used for the notarization of the settlement retains an related document that displays the method by way of which the signature was created.
- Document retention: The ultimate half is to be sure that data are fully stored and in a position to be precisely reproduced by the software program answer used to facilitate the signature.
Signing course of for compliance audits
One of the vital necessary parts for decreasing danger to your group comes within the type of compliance audits.
These are opinions carried out by each inside and exterior entities to be able to consider a enterprise’ adherence to regulatory pointers and necessities for his or her dimension, location, trade, and extra.
As part of these audits, corporations are normally requested to offer detailed accounts for his or her enterprise processes, together with when a doc was modified or accessed and by whom.
With regards to utilizing digital signatures to conduct enterprise, it is advisable to be sure that the signing supplied by your chosen software program answer is ready to give an in depth audit of the signing course of itself. It will present how a buyer or enterprise companion accomplished a enterprise interplay over the web and fulfill the agreements of your personal enterprise audit.
Associated: In search of extra details about compliance? G2 Observe may help you guarantee your group is above board when it comes time for an audit to be carried out.
This might not be crucial if your organization doesn’t fall underneath regulatory oversight. Nonetheless, for those who do, you’ll need to ensure you have all your bases lined with regards to compliance.
Signed and secured
Whatever the enterprise you intend on conducting, the safety considerations of digital signatures could be simply offset by a prudent choice of a software program answer that meets the distinctive organizational and trade necessities of your enterprise.
Following the above compliance guidelines and understanding the completely different safety features can have you properly in your method to understanding precisely what it is advisable to handle any and all dangers.
In search of extra info on the way to defend your knowledge? G2’s information on cybersecurity will arm you with all of the data it is advisable to hold your info safe.



